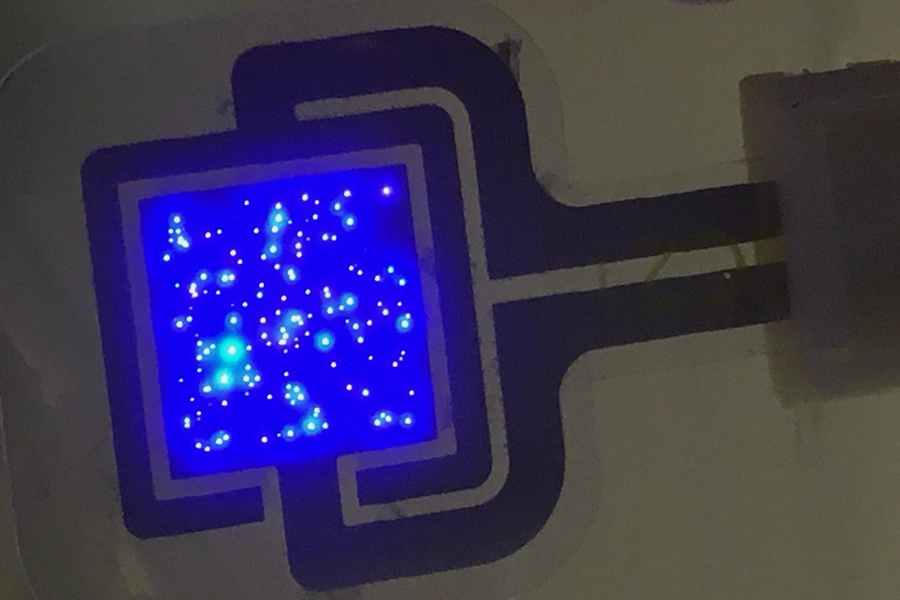
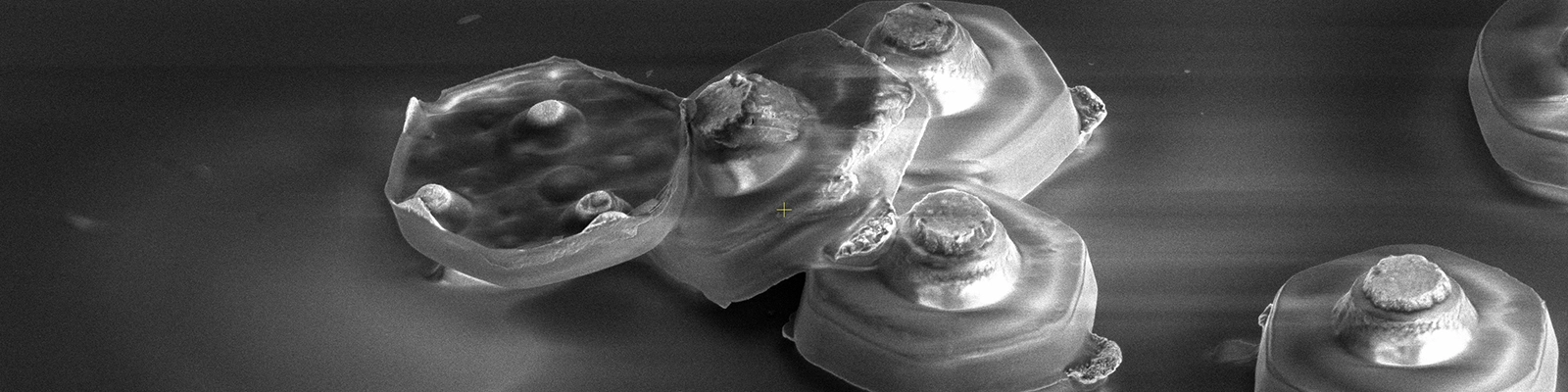
Authentication That Cannot Be Hacked, Cloned, or Compromised

Quantum-grade security through physically unclonable optical structures generating dynamic, per-event passkeys that exist only at the moment of verification—then disappear forever.